UDP flood
A UDP flood attack is a type of denial-of-service attack. Similar to other common flood attacks, e.g. ping flood, HTTP flood and SYN flood, the attacker sends a large number of spoofed data packets to the target system. The goal is to overwhelm the target to the point that it can no longer respond to legitimate requests. Once this point is reached, the service comes to a halt.
What is a UDP flood attack?
The UDP flood is a volumetric DoS attack. Similar to the ping flood, the idea is to overwhelm the target system with a high volume of incoming data. The UDP flood is thus different from the ping of death which crashes the target system by exploiting a memory error and from the SYN flood which ties up resources on the server. One thing all the previously mentioned DoS attacks have in common is that they are intended to overwhelm the target and thus deny it being legitimately used.
The UDP flood has become a matter of public interest in the wake of some spectacular hacking attacks on international organizations. In addition to the Church of Scientology, companies involved in the media and financial sectors have been attacked. The targeted websites and services collapsed under the incoming flood of data and were sometimes unavailable to their users for hours. During these attacks, a powerful tool called the Low Orbit Ion Cannon (LOIC) was used as a weapon to unleash the UDP flood.
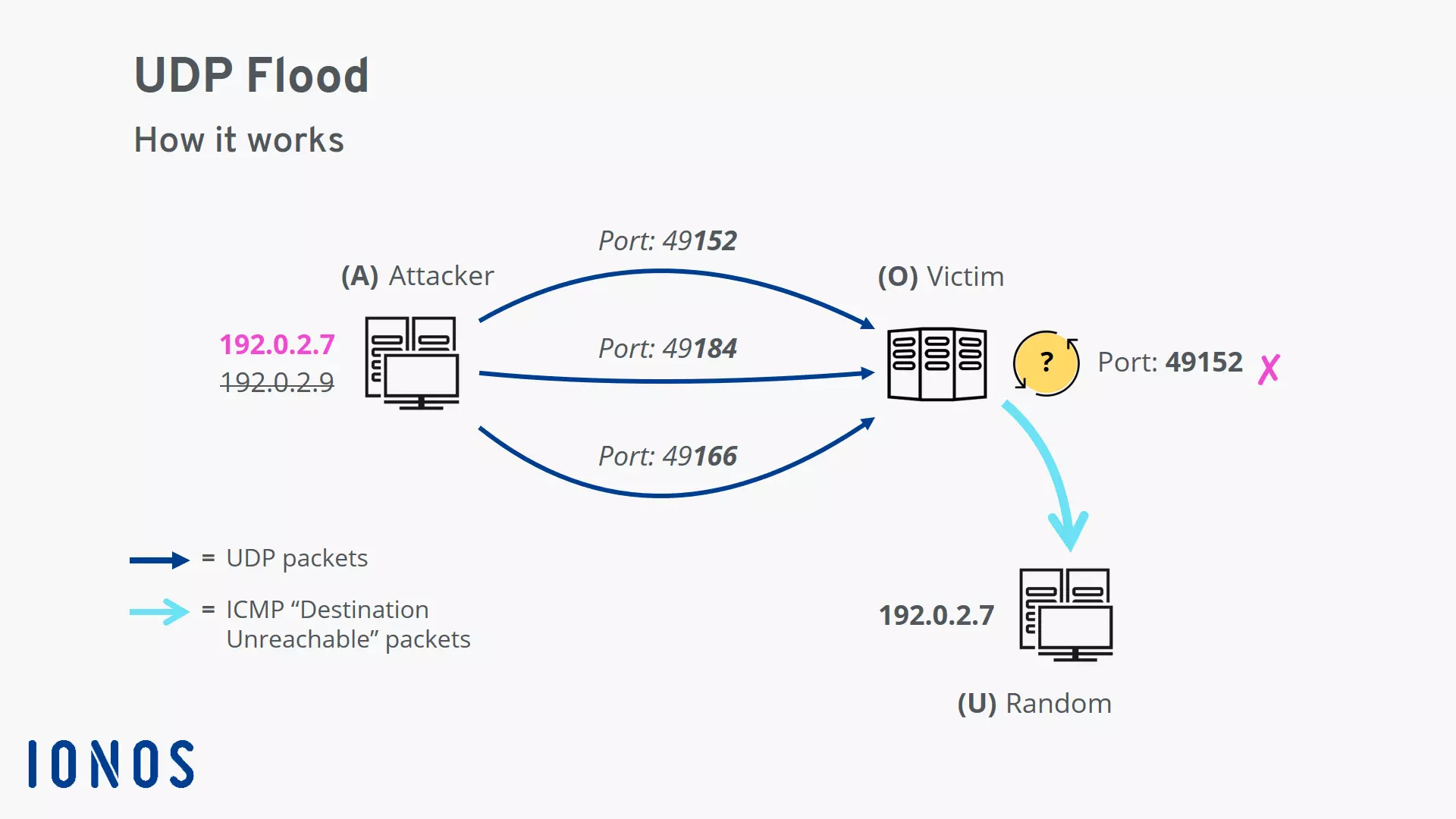
How the UDP flood attack works
The UDP flood attack depends on a particularity of the User Datagram Protocols (UDP) used in the attack. If a UDP packet is received on a server, the operating system checks the specified port for listening applications. If no app is found, the server must inform the sender. Since UDP is a connectionless protocol, the server uses the Internet Control Message Protocol (ICMP) to inform the sender that the packet could not be delivered.
In the event of a UDP flood attack, the following process occurs:
- An attacker sends UDP packets with a spoofed IP sender address to random ports on the target system.
- On the system side, the following procedure must be repeated for each incoming packet.
- Check the port specified in the UDP packet for a listening application; since it is a randomly selected port, this is generally not the case.
- Send an ICMP “destination unreachable” packet to the supposed sender; since the IP address has been spoofed, these packets are usually received by some random bystander.
Security measures to protect yourself against UDP flood attacks
A volumetric network attack can be identified by a sudden spike in the volume of incoming network traffic. Network traffic is routinely monitored by network providers and other specialized parties. This ensures that steps can be taken to minimize the damage if there are any signs of an attack.
The following are some measures that can be taken which provide effective protection against UDP flood attacks:
- ICMP rate-limiting: This limitation placed on ICMP responses is usually done at the operating system level.
- Firewall-level filtering on the server: This allows suspicious packets to be rejected. However, the firewall can also collapse under the strain of a UDP flood attack.
- Filtering UDP packets, except for DNS, at the network level: DNS requests are typically made using UDP. As part of this measure, any other source generating massive amounts of UDP traffic are considered to be suspicious. The packets in question are rejected.
To mitigate imminent attacks, server operators use specialized cloud services such as Cloudflare. These distribute network traffic across a large number of globally distributed data centers. This provides more bandwidth to create a cushion than can withstand the shock of the incoming amount of data in the event of an attack. In addition, data streams are filtered by default to stop a variety of attacks