Ping flood
The ping flood is a type of denial-of-service attack that results in a “denial of service.” You can think of this attack as a prank phone call. A malicious caller keeps calling and hanging up immediately. This blocks the phone line, making it unavailable. Legitimate phone calls can no longer be answered.
With well-known flood attacks like the ping flood, HTTP flood, SYN flood, and UDP flood, a target system is flooded with meaningless requests until it collapses under the load. The ping flood should not be confused with the ping of death which directly crashes the target system without overloading it.
What is a ping flood?
The ping flood is a cyberattack that can target a variety of systems connected to the internet. These targeted systems can be servers as well as routers or home computers belonging to private individuals.
In terms of the technology, the ping flood is based on the Internet Control Message Protocol (ICMP). This protocol and the associated ping command are generally used to perform network tests. A ping flood involves flooding a target computer with ICMP “echo request” packets. If the attacker has more bandwidth than the victim does, the network floods the victim.
How the ping flood works
The basic idea behind the ping flood is simple:
- The attacker sends “echo request” packets in a flood to the victim’s machine.
- The victim’s machine responds with “echo reply” packets.
Each incoming “echo request” packet consumes bandwidth on the victim’s side. Since an “echo reply” packet is sent back for each incoming packet, the amount of data in the outgoing network traffic is equally high. If the attacker has enough bandwidth, they can use up all the available network capacity on the victim’s side. As a result, all legitimate network traffic will be slowed down or completely come to a halt.
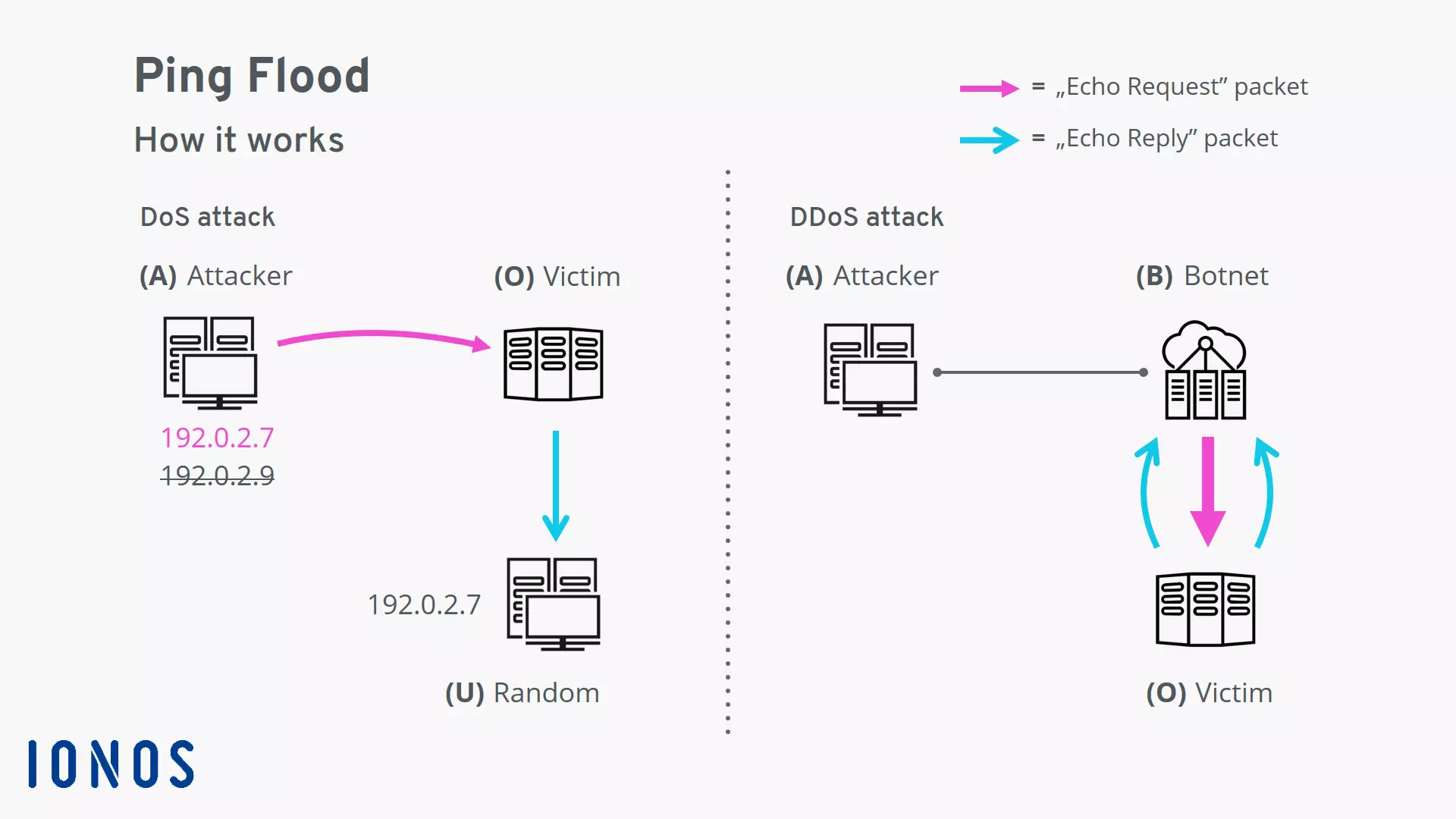
The ping flood can be either a DoS or a DDoS attack depending on whether the attack is being carried out by a single computer or a network of computers.
Ping flood as a denial-of-service (DoS) attack
In the simplest version of this attack, the attacker (A) sends the “echo request” packets to the victim (O) from a single machine. To avoid revealing their identity, the attacker spoofs their IP address. A random computer (U) accessible via this IP address will get caught in the crossfire and be bombarded with the resulting “echo reply” packets. This side effect is known as backscatter. In some versions of the ping flood (e.g. smurf attacks), backscatter is used as the actual weapon.
To ping flood a victim, the attacker uses the ping command or a modern alternative such as the hping tool. The attack is initiated from the command line. The ping flood is launched via a command specifically designed for this attack. For security reasons, we can only show a rough idea of what the hping code looks like here:
Let us examine the options:
- The --icmp option tells the tool to use ICMP as the protocol.
- The --flood option is crucial here. According to the documentation for the hping command, this option results in packets being sent as fast as possible. It also results in the incoming “echo reply” packets from the victim being disregarded and discarded. So, instead of pinging the victim and waiting for the response as is normally done with the ping command, the pings are fired off as quickly as possible.
- The --rand-source option spoofs the sender’s IP address. A random IP address is entered instead of the sender’s real IP address.
The ping flood as a distributed-denial-of-service (DDoS) attack
To launch a distributed ping flood, the attacker (A) uses a botnet (B). The attacker-controlled bots each launch a ping flood against the victim (O) on command. Since multiple computers are now firing pings at the same target, a much higher bandwidth is available on the attacker’s side. Only a highly secure target will be able to withstand such an attack.
In this scenario, since the attacker is not sending the “echo request” packets from their own computer, there is no reason to hide their IP address. The bots are firing the pings from their own addresses instead. The backscatter is returned to the botnet’s zombie computers.
Security measures to protect yourself against ping flood attacks
There are three basic ways to protect yourself against ping flood attacks:
Configure the system that needs to be secured for higher security
Perhaps the easiest way to provide protection against ping flood attacks is to disable the ICMP functionality on the victim’s device. This measure can provide immediate assistance during an attack and be used as a preventive measure to minimize the possibility of attacks.
In addition, the router and firewall can be configured to detect and filter malicious incoming network traffic. The use of load balancing and rate-limiting techniques can also help provide protection against DoS attacks.
Use a cloud-based service to mitigate DDoS attacks
Large providers such as Cloudflare have servers available in globally distributed data centers. If you run your own website, you can route your data traffic through these data centers. This will provide you with much more bandwidth to help absorb DDoS attacks. Data traffic is also filtered by integrated systems such as firewalls, load balancers, and rate limiters.
Use specialized hardware to protect the system
Using specialized hardware to protect your system is only useful for large-scale organizations. These devices offer or combine the functionality of a firewall, load balancer, and rate limiter, and filter or block malicious network traffic.